Access Your Raspberry Pi Remotely & Securely: A How-To Guide
Is the ability to remotely control and monitor your devices from anywhere in the world the key to unlocking the full potential of the Internet of Things? The seamless integration of remote access, especially for devices like the Raspberry Pi, is not just a convenience but a fundamental necessity for modern tech enthusiasts and professionals alike.
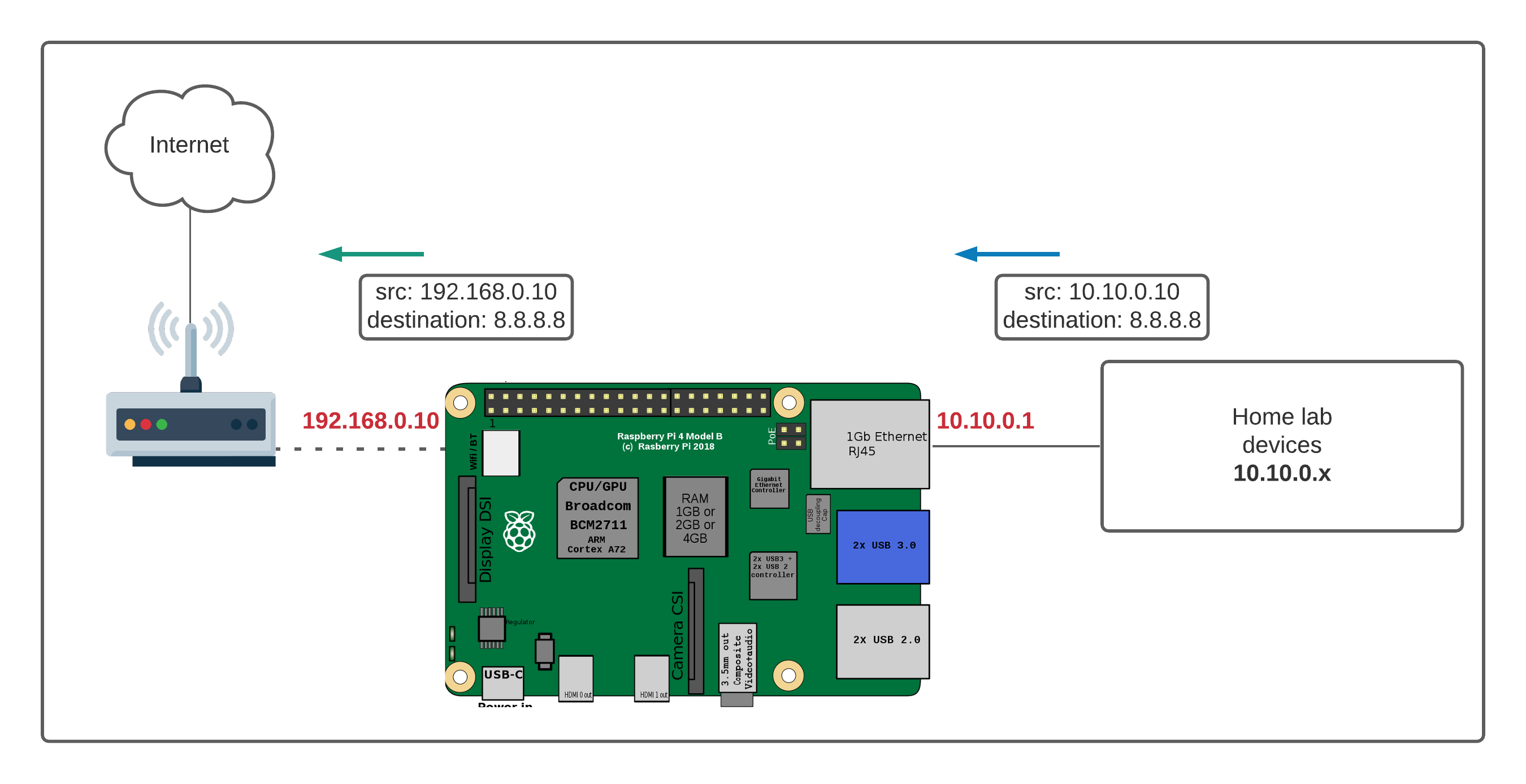
The ubiquity of Internet of Things (IoT) devices has fundamentally altered the landscape of technology, and the ability to manage and control these devices remotely has become an essential skill. Whether it's for home automation, server management, or complex IoT projects, the power to access your Raspberry Pi or other devices from anywhere offers unprecedented flexibility and control. This is particularly true when dealing with devices behind firewalls or Network Address Translation (NAT) routers, where traditional methods often fall short.
The core of secure remote access hinges on understanding and implementing effective methods for circumventing the barriers that routers and firewalls pose. Several tools and techniques have emerged to address these challenges, providing users with the means to establish secure connections without the complexities of port forwarding or other intricate network configurations. These range from secure shell (SSH) and Virtual Network Computing (VNC) to remote desktop protocol (RDP) and innovative services like pinggy.io, which facilitate secure tunneling for seamless remote management.
The integration of your IoT devices with your virtual private cloud (VPC) via cloud connect and the use of TLS (Transport Layer Security) on a2p SMS are some measures that contribute to the security of IoT devices, along with various other software and physical measures undertaken to prevent SIM misuse. In this context, a comprehensive understanding of remote access is not just a technical skill but a critical capability for leveraging the full potential of your IoT devices.
The core of remote access, especially for devices like the Raspberry Pi, lies in its ability to transcend geographical limitations and network configurations. A comprehensive guide on how to remotely connect to a Raspberry Pi behind a router often seems daunting, but the process can be streamlined with the correct tools and steps.
In today's digital age, the concept of remote IoT configurations behind routers has become increasingly popular. The ability to access devices like Raspberry Pi from any location worldwide has become an essential skill. Understanding how to connect to your Raspberry Pi securely, especially behind a router, is crucial for managing servers, automating home devices, or developing IoT projects.
Consider the scenario: You're managing a fleet of remote sensors or a home automation system, and you need to make a change or check the status of your devices. Without remote access, you'd be tied to the local network, significantly limiting your flexibility. With the right tools and techniques, you can securely access your Raspberry Pi and manage these devices, providing unparalleled control and freedom.
Many IoT projects are thriving globally, with many running sophisticated software and performing various amazing tasks. With remote access capabilities, you can monitor your Raspberry Pi, examine CPU, memory, and disk utilization, and identify peak activity on your applications.
One of the most innovative approaches involves using secure tunnels. For instance, you can use socketxp secure SSL/TLS tunnels to securely connect to a private MySQL database or any database in a Raspberry Pi, even behind a firewall.
The official documentation for Raspberry Pi computers and microcontrollers provides a foundation for understanding the hardware and software aspects of these devices. Remote access enhances this foundation by allowing you to interact with your Raspberry Pi from anywhere.
The core methods for achieving remote access typically involve establishing secure connections that bypass the limitations imposed by routers and firewalls. Tools such as SSH, VNC, and RDP provide secure means to manage your device remotely, while services like pinggy.io offer innovative solutions for creating secure tunnels, which simplify the remote management process.
A project may involve a Raspberry Pi connected to a 4G LTE modem. In such cases, remote access becomes essential as it is hard to access the device locally. Remote access will enable you to perform essential functions like running applications, checking logs, or restarting services, no matter your physical location.
There is no need for any restarting for this to take effect. Remote monitoring and alerting for raspberry pi and iot devices, and the ability to provide insights on CPU, memory, and disk utilization, are all elements of effective remote management. In the case of a private MySQL database or any database residing on a Raspberry Pi behind a firewall, secure SSL/TLS tunnels from services like SocketXP can be used.
A reverse tunnel system can be set up to access your Pi from a server. This allows you to establish a secure connection to your device, enabling remote access without requiring complex network configurations.
Remote access offers a multitude of benefits. It allows you to control your Raspberry Pi or IoT device from anywhere, providing real-time monitoring of your device's performance. You can monitor CPU, memory, and disk utilization, and pinpoint peak activity periods within your applications.
The capability to remotely manage devices becomes even more important when you are not on the local network. For instance, when you have services running on a Raspberry Pi, and you need to access them from outside the internal network, remote access is essential. Consider a system you've written that manages external equipment attached to your Raspberry Pi, using a client interface over TCP/IP sockets. With remote access, you can interact with this system, manage your equipment, and monitor its status, regardless of your location.
Additionally, remote access solutions often include methods for securing your connection and protecting your devices from unauthorized access. Tools like SSH, VNC, and RDP provide encrypted connections, ensuring that your data remains private. Secure tunneling services, such as those offered by pinggy.io and SocketXP, further enhance security by creating secure tunnels that protect your data in transit.
Remote access is not just for tech professionals; it's also accessible to beginners. Controlling a Raspberry Pi behind a router using an Android device is an exciting project for IoT enthusiasts. Comprehensive guides walk users through setting up remote access to their Raspberry Pi, enabling control from anywhere in the world.
The integration of your IoT devices with your VPC via cloud connect and the use of TLS (Transport Layer Security) on a2p SMS are some measures that contribute to the security of IoT devices, along with various other software and physical measures undertaken to prevent SIM misuse. In this context, a comprehensive understanding of remote access is not just a technical skill but a critical capability for leveraging the full potential of your IoT devices.
For example, a reverse tunnel system provides a working system to access your Pi from a server. Using this setup, you can establish a secure connection to your Raspberry Pi, allowing remote access without the need for port forwarding or other complex network configurations.
Whether you are managing servers, automating home devices, or developing IoT projects, it's crucial to understand how to connect securely to your Raspberry Pi behind a router. Secure access means more than just connectivity; it means peace of mind, knowing your data and devices are protected.
With the right knowledge and the right tools, remote access becomes a manageable and valuable skill. Enhancing your IoT device control and management from anywhere in the world is no longer a far-fetched concept but a readily achievable reality.
Remember, the key to success is the appropriate configuration and adherence to security best practices. By understanding the principles and applying the right tools, you can establish a reliable and secure remote connection to your Raspberry Pi or any other IoT device, empowering you to manage and control your technology from anywhere.
When dealing with the Raspberry Pi, the official documentation serves as a vital resource for understanding the device's capabilities and how to implement remote access. Additionally, platforms like Stack Exchange provide access to a vast knowledge base where developers can learn, share their knowledge, and build their careers.
Remote access to your Raspberry Pi from anywhere in the world has become an essential skill, and the methods for achieving this are varied and flexible. Remote access to your Raspberry Pi or IoT devices is a crucial skill.